The best (safest) wallet for Bitcoin (BTC)
Cropty Wallet - reliable and convenient Bitcoin wallet for your everyday needs


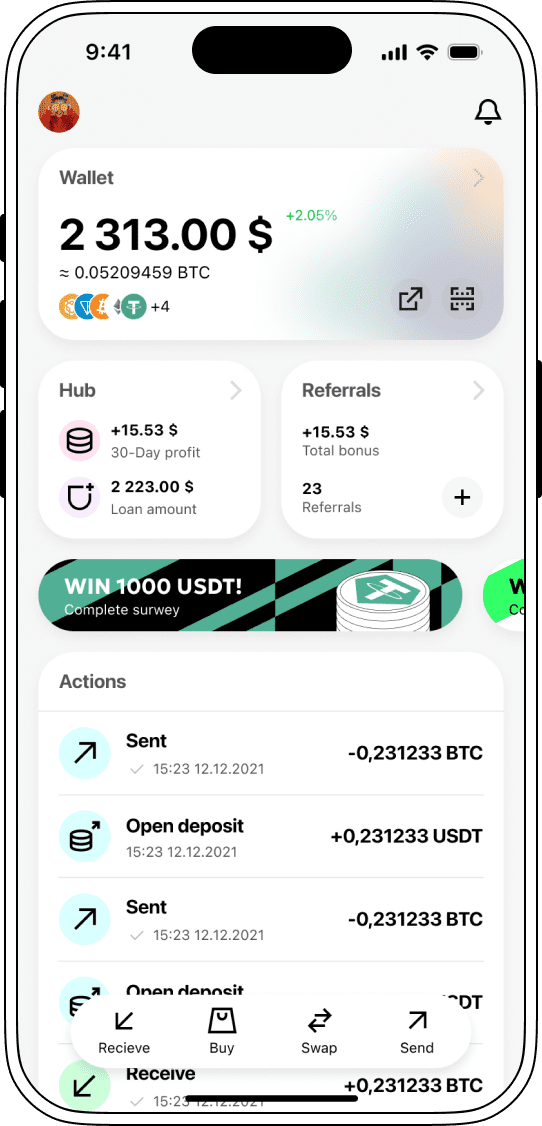

Bitcoin Rates



Does Bitcoin have a wallet?
The Bitcoin official wallet, as commonly understood in other cryptocurrencies, does not exist.
Bitcoin, being a decentralized system, does not have a central governing body that develops and maintains official software.
Instead, there is Bitcoin Core, a desktop application with open-source code created by Satoshi Nakamoto and the development team.
Bitcoin Core is often referred to as the "official" wallet for several reasons:
- It was the first Bitcoin wallet and continues to be supported by the original development team.
- It is open-source software, allowing anyone to verify its security and absence of errors.
- Provides full control over your Bitcoins by giving access to the private key.
- Considered the most secure Bitcoin wallet as it does not store your funds on servers.
However, it is important to note that Bitcoin Core has some drawbacks:
- It can be challenging for beginners to use.
- Requires downloading a full copy of the Bitcoin blockchain, taking up a lot of disk space.
- Not as user-friendly as some other Bitcoin wallets.
There are many other Bitcoin wallets that may be more user-friendly than Bitcoin Core.
Best Bitcoin wallets to Store your BTC






Cropty
Cropty Wallet - is a custodial wallet that offers a simple and secure way to store, manage, and use cryptocurrency. It is suitable for users of any experience level, from beginner crypto enthusiasts to experienced traders and cryptocurrency holders.
Overview
Pros
- Security: Cropty Wallet uses a multi-layered approach to security, including cold storage, secure communication channels, and ISO/IEC certification.
- Ease of use: The wallet has an intuitive interface, making it simple to use even for beginners.
- Additional features: Cropty Wallet offers a range of additional features not available in non-custodial wallets, such as instant fee-free transfers, donation collection, and account recovery.
Cons
- Custodial: Cropty Wallet is a custodial wallet, meaning your keys are held by us. While this may be a drawback for some users, it enables us to provide you with new unique features.
- Limited cryptocurrency support: Cropty Wallet supports a limited number of cryptocurrencies, and you do not have the ability to add your own currency or token to the Cropty wallet
Summary
Cropty Wallet is not just a wallet for storing cryptocurrency. It allows you to:
1. Take out loans secured by cryptocurrency: Get stablecoins using your crypto assets as collateral. Cropty offers convenient and flexible loan terms and low interest rates. Use the borrowed funds for investments, purchases, or other purposes.
2. Earn on stablecoins: Deposit stablecoins into a yield farm and earn passive income by renting them out to other Cropty users with cryptocurrency collateral. It's a reliable and secure way to generate income from your stablecoins, such as USDT.
3. Refer friends and earn: Utilize the Cropty Wallet referral program and receive rewards for each new user you bring in. The more friends you invite, the more you'll earn. Share your wallet link on social media or directly with friends and earn cashback on each of their transactions.

Bitcoin Core
Bitcoin Core - is Bitcoin software developed by Satoshi Nakamoto and a team of developers. Being a desktop wallet with open-source code, it provides full control over your bitcoins, giving access to private keys. Bitcoin Core does not store your keys and data on external servers, making it one of the most secure Bitcoin wallets.
Overview
Pros
- Security: Full control over private keys, fund storage on your computer.
- Decentralization: Does not depend on third-party services, facilitates Bitcoin network operation.
- Open source: Transparency and the ability to verify code for security.
- Functionality: Advanced features such as manually signing transactions.
Cons
- Ease of use: Not suitable for beginners.
- Resource Intensity: A full copy of the Bitcoin blockchain takes up a lot of space on the hard drive.
- Slow synchronization: Initial synchronization with the Bitcoin network can take a very long time.
- Lack of convenient features: Limited set of features compared to other wallets.
Summary
Bitcoin Core is a reliable and secure wallet suitable for experienced users who value decentralization and full control over their funds. However, beginners may find it challenging to use.
Bitcoin Core is best for:
- Experienced Bitcoin users who value security and decentralization.
- Those who want to run their own Bitcoin node and support the network.
- Users who want to have full control over their private keys.
If you're looking for an easy-to-use wallet, you should consider other options.

Ledger
Ledger is a hardware cryptocurrency wallet that provides secure storage for your cryptocurrencies. It operates as a USB device and does not rely on a computer or smartphone for security. Ledger supports over 1800 cryptocurrencies and tokens, as well as allows you to manage your assets with the Ledger Live app.
Overview
Pros
- High security: Ledger uses a security chip with CC EAL5+ certification, providing the highest level of protection for your cryptocurrencies.
- Ease of use: Ledger Live is a convenient application that allows you to easily manage your cryptocurrencies.
- Additional features: Ledger offers additional features such as the ability to stake cryptocurrencies and authentication in Web3 applications.
Cons
- Cost: Ledger is a relatively expensive wallet compared to other hardware wallets.
- Connection to a computer required: To use Ledger, you need to connect it to a computer or smartphone.
- Limited selection of currencies: Ledger Live does not support all cryptocurrencies, so you may need to use other applications to manage your assets.
Summary
Ledger is one of the most popular and reliable hardware wallets on the market. It offers the highest level of security, supports multiple cryptocurrencies, and has a user-friendly interface. However, Ledger is a relatively expensive wallet, and you need to connect it to a computer or smartphone for use.
If you are looking for the most secure way to store your cryptocurrencies, Ledger is an excellent choice. However, if you are looking for a more affordable wallet or do not need to store a large amount of cryptocurrencies, you may consider other options.
Overall, Ledger is a great hardware wallet for those seeking a reliable and secure way to store their cryptocurrencies.

ByBit
ByBit is a centralized cryptocurrency exchange founded in 2018. It offers a wide range of services including spot and margin trading, perpetual contracts, options, Launchpad and more. ByBit is known for its simple interface, high liquidity, and low fees.
Overview
Pros
- Security: ByBit uses cutting-edge security methods such as storing assets in cold wallets, two-factor authentication (2FA), and data encryption.
- Ease of use: The ByBit wallet interface is simple and user-friendly, even for beginners.
- Functionality: ByBit offers a wide range of features, such as the ability to convert cryptocurrencies, track portfolios, and make transactions.
- Low fees: ByBit has some of the lowest fees in the industry.
- Mobile app: ByBit offers a mobile app for iOS and Android that allows you to manage your assets on the go.
Cons
- Custodial: ByBit is a centralized exchange, which means you do not own your private keys.
- Limited cryptocurrency support: ByBit supports a limited number of cryptocurrencies compared to other wallets.
- Support: ByBit Customer Support may be slow and not always responsive.
Summary
Wallet and exchange ByBit is a good option for those looking for a simple and convenient way to store cryptocurrencies. ByBit has a good reputation in terms of security and offers a wide range of features. However, it is important to remember that ByBit is a centralized exchange, which means you do not own your private keys. If you are looking for a more secure option, you should consider using a non-custodial wallet.
Overall, the ByBit wallet is a good option for both beginners and experienced users who are looking for a simple and convenient way to store cryptocurrencies.

Trezor
Trezor Wallet - is a hardware wallet designed to securely store cryptocurrencies. It provides reliable protection for your crypto assets from online threats such as hackers and malware.
Overview
Pros
- Enhanced security: Trezor Wallet provides a higher level of security compared to software wallets.
- Ease of use: The Trezor wallet is easy to use, even for beginners.
- Control over your keys: You will always have full control over your crypto assets.
Cons
- Cost: Hardware wallets Trezor are more expensive than software wallets.
- You will need to carry a physical device to access your crypto assets.
- Limited functionality: Hardware wallets typically have limited functionality compared to software wallets.
Summary
Despite its high level of security, Trezor is easy to use. The wallet interface is clear and user-friendly, even for beginners. All cryptocurrency operations can be performed with just a few button presses.
Trezor is compatible with a wide range of cryptocurrencies, including Bitcoin, Ethereum, Litecoin, Bitcoin Cash, Ripple, and many others. The wallet also supports different platforms such as Windows, macOS, Linux, Android, and iOS (for viewing only).
Overall, Trezor is an excellent choice for those seeking a reliable and secure way to store cryptocurrencies. It is easy to use, compatible with a wide range of cryptocurrencies and platforms.
How to Create an Bitcoin Wallet?
The Most Convenient Way

The Most Stylish Way

The Most Secure Way
What is a best wallet for Bitcoin?
Cropty Wallet - your portal to the world of limitless possibilities of decentralized finance (DeFi) based on Bitcoin!
Cropty Wallet is a custodial wallet, which means that the security of your funds is in the reliable hands of our team of experienced professionals.
Thanks to this, we can offer you a range of additional benefits and useful features:
- Instant Bitcoin transfers with no fees: Send Bitcoin to other Cropty Wallet users without delays or extra costs.
- Convenient donations collection: Create useful public links to receive Bitcoin donations.
- Easy access recovery: Don't worry about losing your data or keys! We will help you restore access to your wallet.
- Bitcoin-backed loans: Get USDT by using your BTC as collateral. You no longer need to sell your Bitcoins to unlock the funds invested in them.
Cropty Wallet is:
- Ease of use: Manage your BTC easily and intuitively.
- Reliability: Your funds are safeguarded by cutting-edge security technologies.
- Versatility: Use Bitcoin in any way you like - from payments to investments.
The best Bitcoin wallet for Android
Cropty Wallet is an excellent solution for storing Bitcoin on Android devices, providing a high level of security, ease of use, and wide availability.
Security is ensured by a system that stores access keys outside the user's device and includes two-factor authentication when conducting transactions.
In addition, Cropty Wallet is easy to learn and perfect for everyday Bitcoin operations. Users can easily send, receive, and store Bitcoin, as well as exchange them for other cryptocurrencies.
The Cropty Wallet app is available for free download to all Android users.
The best Bitcoin wallet for iOS (Apple)
If you need a simple, convenient, and secure Bitcoin wallet for iPhone, Cropty Wallet is the perfect choice!
In terms of security, Cropty Wallet ensures the protection of your assets by storing private keys off-device and adding biometric authentication for each transaction, ensuring the highest level of security.
In terms of convenience, Cropty Wallet is designed with user needs in mind: the app interface is simple and intuitive, making it excellent for everyday Bitcoin operations.
As for availability, Cropty Wallet is offered for free to all iOS users. Download the app today and start using it for Bitcoin transactions!
The best cold storage wallet for Bitcoin
When choosing a cold wallet to store Bitcoin, it is important to pay attention to security, usability, and reliability. In this context, Trezor and Ledger are two of the most recommended and appealing options.
Both devices offer a high level of protection against cyber threats as they operate offline, isolating private keys from the internet. Additionally, they provide ease of use and have a solid reputation within the cryptocurrency community. Therefore, choosing Trezor or Ledger can ensure you maximum satisfaction in securely and conveniently storing your Bitcoin.

Most secure crypto wallet for Bitcoin
Although there are many options for storing bitcoins, a paper wallet is often considered one of the most secure options. This is because the private keys of bitcoin addresses are stored on physical paper not connected to the internet, making them inaccessible to hackers.
We recommend using a paper wallet for long-term storage of significant amounts of cryptocurrency. If you are interested in creating your own paper wallet, we suggest using our paper wallet generator, which allows you to safely create and print it.

How to buy Bitcoin - Beginner's Guide
Want to add Bitcoin to your cryptocurrency portfolio? There are two common ways: P2P trading and exchange services.
P2P Trading
Buying directly from other users: Choose a seller, agree on the terms, transfer fiat currency (e.g., dollars) to their account. After payment confirmation, the seller will send you Bitcoin to your wallet.
Advantages:
- Low fees: P2P platforms usually charge less than exchange services or exchanges.
- Variety of payment methods: Buy Bitcoin for dollars, euros, and other currencies using cash, bank cards, electronic wallets, or bank transfers.
In our article, we have detailed how to buy Bitcoin on the P2P market.
Exchange Services
Simple and fast method: Specify the desired amount of Bitcoin, your wallet address, choose a payment method. The service will automatically exchange your fiat currency for Bitcoin and send it to your wallet.
Advantages:
- Ease of use: Clear interface even for beginners.
- Fast transaction processing: Transactions are usually processed within minutes.
- Anonymity: KYC is often not required, ensuring the anonymity of purchases.
In our article, we have detailed how to buy Bitcoin through an exchange service.
Which method to choose?
P2P trading is suitable if you want to buy Bitcoin with low fees and a variety of payment methods. Exchange services, on the other hand, offer a simple and fast option, but the exchange rate may be less favorable.
Important: Before buying Bitcoin, make sure to read reviews about the P2P platform or exchange service to protect yourself from scammers.
Where is the safest place to buy Bitcoin?
Depending on your chosen method of acquisition, we can offer various reliable platforms for purchasing Bitcoin.
If you prefer P2P trading, we recommend checking out the P2P trading section on ByBit cryptocurrency exchange, where numerous sellers, favorable exchange rates, and a trustworthy Escrow system are available.
For those who prefer using exchange services, we recommend using BestChange exchange monitor service, which can help you choose an exchange with the best rate and convenient payment methods for acquiring Bitcoin.

What is Bitcoin?
Imagine digital money that is not controlled by any bank or government. This is Bitcoin, or BTC.
It is a cryptocurrency created in 2009 by a programmer using the pseudonym Satoshi Nakamoto. It is the first and most well-known digital currency, operating on blockchain technology. Bitcoin is a decentralized system that is independent of corporations or governments and uses cryptography to secure transactions.
Here are some key points:
- Decentralized: No one owns or controls Bitcoin. The network operates on millions of computers around the world.
- Digital: Bitcoin exists only electronically. You do not have physical coins or banknotes.
- Secure: Cryptography protects transactions and makes them nearly impossible to counterfeit.
- Global: Bitcoin can be used to send and receive payments anywhere in the world.
- Pseudonymous: Transactions are public, but your identity is not linked to your Bitcoin address.
How Bitcoin works:
- Mining: Specialized computers solve complex mathematical problems to "mine" new Bitcoins and create blocks of transactions to add to the blockchain.
- Blockchain: All transactions are stored in a public ledger called the blockchain.
Why Bitcoin is useful:
- Fast and Cheap Payments: Bitcoin transfers, especially international ones, can be faster and cheaper than traditional bank transfers.
- No Intermediaries: You can send and receive Bitcoin directly, without the involvement of banks or other third parties.
- Protection Against Inflation: The supply of Bitcoin is limited, making it resistant to inflation.
- Investment: The value of Bitcoin has significantly increased over the years.

How to sell Bitcoin?
The process of selling Bitcoin is similar to the above-described buying process. You should choose the appropriate exchange or platform for trading, register on it, go through the verification process, transfer Bitcoin to your account, and place a sell order. To sell Bitcoin, you can use the same trading platforms as you did for its purchase.

Bitcoin exchange is the process of converting Bitcoin into another cryptocurrency or fiat currency. You can perform exchanges on cryptocurrency exchanges such as ByBit, as well as on centralized or decentralized exchange platforms. To choose a suitable exchanger with a favorable rate, use the BestChange service.

How to stake BTC?
Staking Bitcoin (BTC) directly is not possible, as this cryptocurrency operates on the Proof of Work (PoW) consensus algorithm, not Proof of Stake (PoS).
In PoW, miners use computational power to solve complex mathematical problems and are rewarded with BTC for doing so. Staking, on the other hand, involves locking coins for a specific period to support network operations and earn rewards for it.

How to earn BTC
There are several ways to earn and multiply your bitcoins, for example:
- Mining - one of the most common methods. Use your computational power to verify transactions and add them to the blockchain, earning rewards in the form of new Bitcoins.
- Cropty Referral Program - earn cashback from BTC transaction fees made through our wallet by inviting friends to use Cropty. You will receive income from each transaction they make using Cropty Wallet.

Bitcoin mining is the process where participants in the Bitcoin network (miners) solve complex mathematical problems to add new blocks of transactions to the blockchain and receive rewards in the form of new bitcoins.
Here’s how it works:
- Transactions: Users send bitcoins to each other, creating new transactions.
- Transaction Collection: Miners collect these transactions into the mempool, from which the transactions are then packed into a new block.
- Adding a hash: A hash is added to the block - this is a unique code that represents a "fingerprint" of all transactions in the block.
- Hash Search: Miners use their computers to iterate through random numbers, trying to find a number whose hash meets specific requirements.
- Finding a hash: The first miner to find the correct hash wins the right to add a block to the blockchain.
- Reward: This is the reward a miner receives in the form of new bitcoins and transaction fees included within a block.
The process of searching for a hash is called mining.
- It requires significant computational power, so miners often use specialized hardware (ASIC miners) optimized for solving these tasks.
- Mining difficulty is constantly adjusted to maintain the average time to create a new block at around 10 minutes.
- The more miners in the network, the more difficult mining becomes.
In addition to mining new bitcoins, mining performs important functions
- Provides network security: Miners verify transactions and add them to the blockchain, ensuring the immutability and authenticity of the information.
- Decentralizes the network: Mining does not depend on any central authority, making the Bitcoin network resistant to censorship and manipulation.
Important:
- Mining can be profitable, but it is not a guaranteed way to earn money.
- Mining profitability depends on many factors, such as mining difficulty, Bitcoin price, and electricity costs.
- Before starting to mine bitcoins, carefully study all risks and assess your abilities.
How long does a Bitcoin transaction take?
Transaction confirmation time for Bitcoin depends on several factors:
- Network congestion: The more people use Bitcoin, the more transactions await processing, and the more time it takes to confirm a transaction.
- Transaction fees: Higher transaction fees incentivize miners to include transactions in blocks faster.
- Transaction size: Larger transactions typically require more confirmations.
On average, a Bitcoin transaction confirmation takes from 10 minutes to several hours.

Learn more about BTC transaction fees

Reviews about Bitcoin wallet
More coins































































